Reports are surfacing all across the tech world that Intel chips suffer from a fundamental flaw that affects all of the company’s modern CPUs. It’s impossible to fix with a chip-based update, and requires a software-based solution through the operating system, which in turn causes a performance hit of up to 30 percent.
While the bug is simple enough to deal with through a Windows, Linux or Mac OSX patch, the performance hit is severe. Microsoft is expected to address the bug in its monthly “Patch Tuesday” update, while Linux patches have already been distributed to users.
The circumstances of the bug remain under wraps due to the severity of the vulnerability, which if discovered, could allow hackers to penetrate major web platforms at an OS level.
To simplify explanations provided by websites like Python Sweetness and The Register, the bug allows everyday software to “illegally” access contents in protected kernel memory. The kernel is essentially the control center of a CPU, which carries instruction sets used by software.
In other words, allowing a piece of software to access this protected memory is capital Not Good, as a hacker with bad intent could use it to inject all manner of malicious software into a computer, or gain backdoor access.
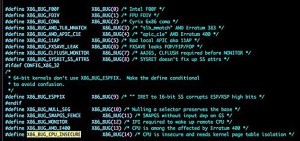
The only way to “fix” the issue without rebuilding the architecture of the Intel chip itself is to implement a sort of barrier in front of the kernel to prevent regular software from accessing it called the “Kernel Page Table Isolation,” which renders the kernel invisible to those apps. Developers at Microsoft, Apple, and Linux distros are working on it.
(Click image to enlarge)
However, the issue with added security layer comes at the cost of performance. In the best-case scenario on Linux, performance takes a minimum hit of 17 percent. On Windows, that performance handicap can be 30 percent or higher. Newer processors may have the impact somewhat lessened, but not by much.
The slowdowns can occur even in typical workloads, according to Python Sweetness.
Unfortunately, it is dangerous to avoid upgrading, as the security vulnerability is significant. Virtualized environments, such as cloud servers operating on Amazon Web Services and Microsoft Azure, are ripe for attack. Both services are set for scheduled maintenance next week.
Neither service provided an explanation for the downtime, leading software experts to speculate that the companies may be implementing software fixes to deal with the bug. Some operating systems may have to be reengineered from the ground up to fix the problem.
The problem does not affect AMD processors due to security protections baked within the company’s processors. If you’re running a Ryzen, you should be good to go.
Source: dangerous.com
Ask me anything
Explore related questions