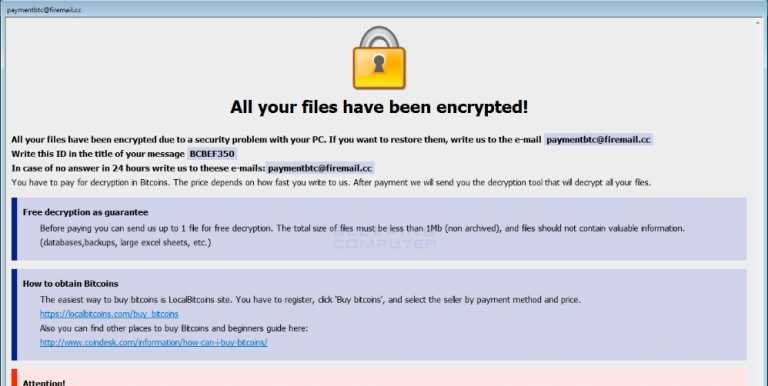
On Thursday a new variant of the Dharma Ransomware was discovered that appends the .cmb extension to encrypted files.
The Cmb variant of the Dharma Ransomware was first discovered by Michael Gillespie when he noticed samples uploaded to ID Ransomware, After tweeting about it, Jakub Kroustek replied with a hash to the sample.
Unfortunately, there is no way to decrypt files infected with the Dharma Cmb Ransomware variant for free. For those who wish to discuss this ransomware or receive support, you can use the dedicated Dharma Ransomware Support & Help topic.
Distributed through hacked Remote Desktop Services
The Dharma Ransomware family, including this Cmb variant, is installed manually by attackers hacking into computers over Remote Desktop Protocol Services (RDP). The attackers will scan the Internet for computers running RDP, usually on TCP port 3389, and then attempt to brute force the password for the computer.
Once they gain access to the computer they will install the ransomware and let it encrypt the computer. If the attackers are able to encrypt other computers on the network, they will attempt to do so as well.
How the CMB Dharma Ransomware encrypts a computer
When the Cmb ransomware variant is installed, it will scan a computer for files and encrypt them. When encrypting a file it will append an extension in the format of .id-[id].[email].cmb. For example, a file called test.jpg would be encrypted and renamed to test.jpg.id-BCBEF350.[paymentbtc@firemail.cc].cmb.
It should be noted that this ransomware will encrypt mapped network drives, shared virtual machine host drives, and unmapped network shares. So it is important to make sure your network’s shares are locked down so that only those who actually need access have permission.
Read more HERE
Ask me anything
Explore related questions